Cyberattacks, whether they are ransomware attacks motivated by monetary gains or nefarious attempts to disrupt business and government operations and obtain information for a nation-state, continue to rise in 2019.
BakerHostetler’s privacy and data protection team released its Data Security Incident Response Report. The report contains incident response metrics applicable to all enterprise entities and recommendations that can help organizations identify and prioritize measures to reduce digital risk exposures.
“Privacy laws around the globe are shifting the way companies prepare for and manage data breaches. Our report highlights the collision of data security, privacy and compliance, and provides guidance on how companies can take action on key response items,” said Theodore J. Kobus III, leader of BakerHostetler’s privacy and data protection team.
According to the report, about 5 percent of the firm’s 750 network intrusion incidents it helped entities address in 2018 were government resources.
3 Network Intrusion Incident Trends
#1 Phishing & 2 Key Defenses
Phishing remains the leading cause of incidents tracked by the report, and roughly one-quarter of all incidents BakerHostetler responded to for the year were caused by:
- Lost devices
- Inadvertent disclosures
- System misconfigurations
The firm mentions two best practices to implement quickly:
Across the 750 incidents analyzed, 55% had employees involved as the responsible party, through a mix of simple mistakes, to falling for phishing or being socially engineered, according to the firm’s announcement.
The report also notes, as one of 14 final action items, that organizations should pay attention to cloud access configurations.
“Raising employee awareness and employing multifactor authentication are still two of the best defenses to address the employee risk factor,” said Kobus.
#2 Forensic Cases & Costs Up, Investigation Time Down
Forensic investigations, cited as a key 2019 public safety prediction, are on the rise. In 2018, forensic investigations were conducted in 65% of all incidents the firm analyzed in its report. There was a 14 percent increase over the prior year.
While the average cost of forensic investigations decreased from an $84,417 average the prior year to a $63,001, costs of network intrusion investigations rose from $86,770 to $120,732.
“There are a few reasons why the overall cost of forensics dropped. Last year, we saw a number of incidents resulting from ransomware and gaining remote access to email mailboxes to execute a fraudulent wire transfer. Neither of these scenarios generally results in large forensics expenses. For ransomware, many of the incidents are still contained and do not necessarily require a broad review of the entire network. For the wire transfer matters, most of the expenses relate to reviewing the contents of the mailbox to determine any potential notification obligations.
“Conversely, with network intrusions, access to the entire network is potentially at issue and the costs associated with gaining visibility into the entire network are often much greater -- especially because many companies don’t already have endpoint monitoring tools in place to facilitate with gaining that visibility. On top of that, the forensics analysis around what was actually accessed or exfiltrated is more complicated,” Kobus told Gov1 by email.
In 2018, 74% of incidents were detected internally, a marked rise from only 52% in 2015, according to the announcement. The firm added that more organizations are investing in security tools that can assist in investigating network security incidents, but most require third-party support.
A historical look at incident response timelines in the data showed improvements in the time-to-complete metric for forensics investigations. While containment is steady at six-to-eight days for five years, forensic investigations were significantly reduced from 47 days in 2015 to 28 days in 2018.
#3 Data Breach Notification Regulations Activate Government Oversight
There is increasing scrutiny from regulators. Every state in the U.S. now has its own law governing data breach notification requirements, and state attorneys general continue to increase their oversight activities and expand their enforcement regimes through new state laws or increased use of existing laws.
In 2018, 34% of the incidents that required consumer notification received inquiries by state attorneys general, compared to just 16% in 2015. Other enforcement agencies are also becoming more active, particularly in the financial and insurance areas. The report indicates that state and federal financial and insurance regulators are some new entities that have not traditionally been active in data privacy investigations.
Despite new regulations pushing entities to notify quickly, the report shows
a 67% increase in the time from discovery to notification, averaging 40 days over
the past few years to 56 days in 2018.
The Reports 5 Key Findings & Recommendations
#1 Get ahead of the compliance curve
New laws are inevitable, so try to anticipate what will be enacted, because most new laws borrow heavily from existing laws and core privacy and security principles: transparency, confidentiality, integrity, availability, fairness and data minimization.
#2 Conduct M&A due diligence
Evaluate digital risks to assess the target’s privacy compliance and security posture before the merger or acquisition. Compromise assessments before or immediately after acquisitions of new entities help find undetected issues and support integration efforts.
#3 Litigation persists
Class actions arising from data breaches or that allege violations of privacy laws continue, and outcomes remain inconsistent, with outliers in both court rulings and settlements. Derivative actions are becoming more popular, based on both data breaches and statutory compliance grounds. The plaintiffs’ bar continues to be creative to survive motions to dismiss, and some are coordinating efforts with regulators.
#4 Use “compromise response intelligence”
Leverage the misfortune of others to identify emerging risks: Identify the issues affecting other organizations and address them before you become a victim.
Towards the end of 2018, the ransomware threat to organizations, including local governments, is evolving:
“Instead of pushing out commodity malware broadly, threat actors are buying access to environments from other threat actors. When they get into the network, they may find and delete backups before deploying the ransomware to many devices. The threat actors are also paying more attention to identifying their victims and demanding a higher ransom.”
#5 Nation-state attacks drawing more attention
Nation-state cyber operations continue to support espionage, economic development (through IP and trade secret theft) or sabotage, and collateral damage to unintended victims has been significant. It has become increasingly difficult to differentiate between the tactics, techniques and procedures used by nation-state actors and criminal actors. Good data on how often these attacks occur is hard to find, partly because they go undetected or unreported.
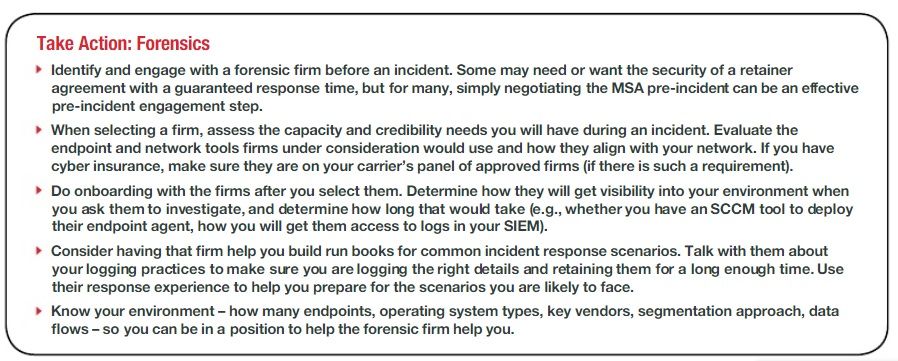
The report, which contains graphs and charts, also concludes with 14 action items enterprise organizations can take to reduce network intrusions and lower their digital risks.
Request the full report on BakerLaw.com.
About BakerHostetler
BakerHostetler is a leading national law firm with more than 970 lawyers in 14 offices and is widely regarded as having one of the leading data privacy and cybersecurity practices. Our attorneys have managed more than 3,500 data security incidents for some of the world’s most recognized brands. Our privacy and data protection team’s work extends beyond incident response and is one of the largest of its kind. In addition to privacy and data breach issues, we handle regulatory compliance, GDPR and other cross-border issues, marketing and advertising, security risk assessment, regulatory and class action defense.



